"Out front, we find a grand, feelgood gloss, extending around us a warm hug of protection. But behind the curtain, it's just another cybertech company pimping us out to the preds."
For years, we've been wondering whether the Startpage search engine might warrant a little more scrutiny. Whether the notion of "actual Google without the tracking" should perhaps be tentatively subjected to the old adage:
"If it sounds too good to be true... It probably is."
But Startpage's recent release of a so-called "privacy protection" extension for browsers, might just have burst the brand's carefully-cultivated integrity bubble for us.
SO, ER, WHY MAKE A TRACKER-BLOCKER?
The question marks over Startpage's privacy commitment have grown in size of late. In part, that's because we've been moving into an era of privacy by design. In other words, using setups that can't collect our data, rather than setups that can, but merely claim that they don't. As the volume of cybertech data-fraud has ballooned skyward, more client-side processing has emerged to combat the mistrust. But for Startpage, the fact that we increasingly distrust tech brands' promises has been very bad news.
In some ways we've arrived in a post-privacy world where we know that words are just words, and that nothing any tech brand says really means anything unless it's backed up with a transparent system we can personally audit. If they're ALL liars, then unless the tech is shifting to the client side, we might as well just use the best tools, regardless of their supposed ethics. And Startpage does not fall under the heading of "best tools".
Maybe that's why Startpage thought that now would be a good time to introduce a client-side tool of its own? A browser extension that reputedly protects our privacy by blocking the trackers that follow us around the web. Sounds great in theory - even if the market is already awash with alternatives.
But more importantly, such an extension would finally give us a graphic insight into Startpage's privacy commitment. With the jiggery-pokery ported across to the client-side, we, the public, would become eyewitnesses in a Startpage privacy-protection regime. How obsessive is Startpage about protecting our privacy? It was time to find out.
RECENT BACKGROUND
I can't say I installed the extension without trepidation. In recent years, Startpage has been busy forcing unnecessary JavaScript dependencies into its pages. A privacy degradation which directly contradicts the FSF's Free JS campaign. Free JS calls for all sites - especially those that consider themselves ethical - to make their pages function without the need for active scripting. Startpage's activity has been particularly passive-aggressive against this campaign, since they already had pages that worked perfectly well without JS, then broke them on purpose so they no longer would. Something I call script-jacking.
Meanwhile, Startpage quietly fell into the hands of System1 - an under-the-table, AI-driven, ad-targeting cockroach with very high-tech data-guzzling capability. There's still been no rational explanation as to why data-crazed surveillance capitalists would want to buy a search engine that is supposedly opposed to collecting data. Startpage has insisted that System1 is only an investor and has no executive control over the search brand, but that would only make the buy-in even more nonsensical.
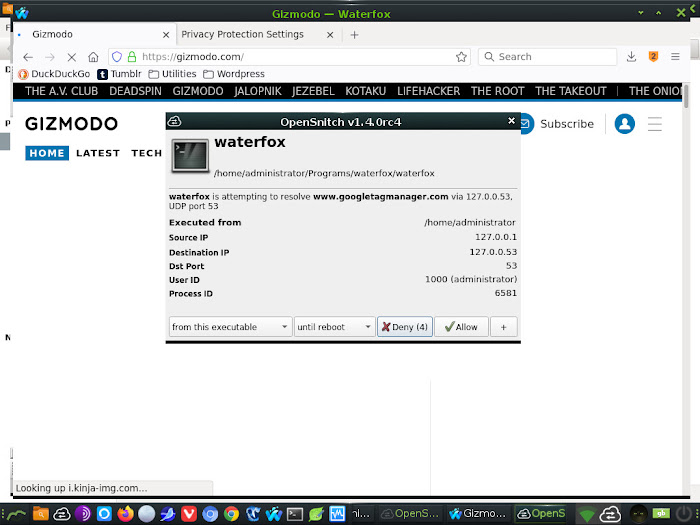
Just months after officially buying into Startpage, System1 also acquired the Waterfox web browser, which now phones home to Startpage.com. Waterfox's network connections to Startpage completely contradict Startpage's pledges of data minimisation. Clearly, Waterfox does not inherently need to contact Startpage in order to launch to a blank tab.
So either Startpage is now under the full control of System1, and has no say in how the monumentally opaque data company chooses to leverage the Startpage servers, or Startpage has separately made a data transfer agreement with Waterfox. Whichever way, it looks pretty damning for a brand that's done nothing but shout about data minimisation for the past decade and a half.
[UPDATE - February 2022: On reassessment I've established that Waterfox does not inherently phone Startpage. It natively phones Waterfox. However, Waterfox does phone Startpage on launch if you have the Startpage Privacy Protecton extension installed. The call is not related to updates as it happens when extension updating is disabled. This is just one of multiple calls to Startpage made by the supposed "privacy extension" - none of which appear to be necessary beyond mere collection of data. The Startpage extension also makes a call to Startpage upon installation, and a call to Startpage whenever you click its icon for info - which is not necessary for the extension's functionality and is therefore evidently just a snitch call. END OF UPDATE]
THE NEW BROWSER EXTENSION: STARTPAGE PRIVACY PROTECTION
Startpage's Privacy Protection extension, to which I'll mainly hereinafter refer as SPP, surfaced in the Firefox add-ons store during December 2021, but only got its concerted launch this week. So what's in this for Startpage? Have they created this FREE, no-ads tool, with no apparent revenue stream, simply because they're nice guys?
Well, you can believe that if you want, but if SPP were to catch on, it would allow Startpage and System1 to access a much wider catchment of browsing data than the group can currently access via Waterfox. Simultaneously, it would drive an increase in default search conversions, whilst potentially also facilitating a paid whitelisting scheme in the background. That, I believe, is the intention. Blocking trackers is clearly not the priority, as you'll see.
SPP has multiple bugs, which don't reflect well on Startpage's competence, but in the case of this extension, fixing bugs would be pissing in the wind…
Excuse this analogous mini-digression, but in the UK's TV archives there's a wonderful vintage Candid Camera sequence where an "asset-stripped" car is rolled down a hill into a garage, with the driver complaining that he's having mechanical trouble. After much peering under the bonnet and conferring among the baffled garage staff, one eventually plucks up the courage to announce the cause of the trouble…
"There's no engine in it."
I reacted somewhat similarly when I delved into the workings of the Startpage privacy extension. The initial blocklist is only 1,242 entries long, and many of the URLs are not actually blocked from the page load. Their settings only stop cookie transfer. So if you already block third-party cookies in your browser, the cookie-only presets are just duplicating existing blocks. By comparison, the uBlock Origin extension compiles lists of tens of thousands of trackers, assembling what must approach 100,000 potential blocks in total.
FLAWED BLOCKING METHOD
SPP does slowly add to its blocklist. Its blocking method is like that of the EFF's Privacy Badger, in that it seeks to identify trackers cumulatively, based on machine learning. There are five main problems with this cumulative, behavioural method…
Number one, you're relying on simple software, as opposed to a group of intelligent human beings, to work out what is or is not a tracker - and we should note here that the trackers' software is vastly more expensive and sophisticated than the blocker's software, giving the trackers the upper hand.
Number two, it takes a very long time for a cumulative blocklisting model to start offering sufficient tracking protection.
Number three, behavioural blocklisting can be defeated by behaviour-cloning. That is, the trackers can assess which tracking tools evade the block and then clone their behaviour so that their own tools can evade the block also.
Number four, cumulative blocklisting creates a significantly unique blocklist per user, which can in itself potentially identify the user to sophisticated and pervasive surveillance setups. The data created during the listbuilding process can also potentially be harvested by the extension provider and sold on. Let us not ignore that the data derived from a cumulative blocking mechanism would be of immense value to actual trackers seeking to circumvent blocks. We should by no means dismiss the idea that they would pay very handsomely for it.
And number five, if you change your browser, or your device, or for any reason have to re-install, you go back to square one and lose all of the cumulative blocking capability the extension built up. The previous state is basically un-reinstallable, if that's a word.
You can then start a list of secondary problems. For example, in relation to point five, the consumer is compelled to use one browser only, which then defeats the privacy tactic of brand disloyalty - i.e. using multiple browsers to increase resistance to fingerprinting. And so on. So even by basic design, SPP is a poor method of blocking trackers. And the deeper you look under the bonnet, the more pieces of the engine you discover are missing. Here are some of the fundamental omissions in Startpage Privacy Protection. Unlike other tracker-blockers…
SPP does not tell you what it's letting through its gate, so you have no native means of assessing whether it's doing its job properly.
SPP does not let you add your own blocklist, so there's no way to shortcut the long haul of cumulative prevention.
SPP does not let you blacklist individual domains, so if there's a site you know is tailing you and strongly object to, tough. It's most telling that Startpage managed to incorporate a user-controlled allow-listing feature, but not a user-controlled blocklisting feature. A privacy company that wants users to whitelist trackers but not blacklist them? Looks more like the behaviour of a data company to me. Much akin to a bad cookie-consent form where blocking is exponentially more difficult than enabling. Except Startpage goes one better (read one worse), making user-initiated blocking outright impossible.
SPP has no means to block specific tracking protocols. You can't, for example, set it to block JavaScript, set it to block tracking pixels, or set it to block remote fonts.
In short, you have minimal control over what SPP blocks - deliberately so in my opinion.
True, minimal blocking is better than no blocking at all, so we can't write off SPP just yet. But there's more downhill sliding in store. Yep, this gets worse…
SPP incorporates some full-on whitelisting, and in a product designed to machine-learn what is or is not a tracker, this is difficult to explain beyond paid exclusion. The fully-whitelisted resources include URLs from Medium and the ad baron Criteo. These exclusions seem bizarre, since they're by no means the most critical dependencies on the web. I mean, if you're gonna whitelist on the basis of mass public dependency (which is the typical whitelisting excuse), you'll be whitelisting Google services, Amazon services… But SPP doesn't fully whitelist any Google or Amazon services. Which begs the question: why Medium? Why Criteo? It certainly can't be explained on ethical grounds either. So are these paid exclusions?
And what about the massive underground AI tracker 1PlusX, comin' atcha via the cryptic tagger.opecloud.com? SPP full-on whitelists that monster too. uBlock Origin won't even let me access the tagger.opecloud.com domain as a first-party visitor, due to blacklistings on two separate contributors' blocklists.
From the user's viewpoint, there can be absolutely no justification for Startpage letting 1PlusX through the gate. It's purely an aggressive tracker. It doesn't do anything for the visitor. And remember, Startpage have not merely neglected to add tagger.opecloud to their blocklist. They have specifically given it full whitelisting clearance - including permission to drop cookies. We surely have to conclude, at this point, that Startpage's agenda is not to facilitate user-privacy, but to create an illusion of user-privacy.
So, we done yet? Nope. More to come I'm afraid. Startpage Privacy Protection phones home every time you click its icon in the browser. You just knew that was coming, didn't you?
In response to this, I firewalled the Startpage.com domain to prevent the network connections. And?… And nothing. Extension still works. Makes absolutely no difference at all to the functionality. Which means?… Yep, it doesn't need to contact Startpage. The reason it is contacting Startpage, I can only assume, is that Startpage/System1 are COLLECTING DATA. What other point would there be in making network connections that do nothing for the user?
THE IMPLICATIONS
As I said earlier, SPP differs from Startpage search in that it does its work on the client side - not the server side. With the search engine, you're sending information to Startpage, and then letting the company do whatever they do behind the scenes, in secret. But with a product that runs on the client side - namely Startpage Privacy Protection - the reality cannot be hidden from us in the same way. If we look hard enough, we get to see precisely what that product is and is not doing to protect our privacy.
And the observations are damning indeed. We're seeing blatant predators welcomed through the door - whitelisted even - in a culture of smoke 'n' mirrors which seeks to divert attention away from the rampant deficiencies and deliberate trap doors in the system. We're seeing undisclosed network connections which are not justified by functional need. Basically, we're seeing behaviours that align more closely with the goals of a data company than the goals of a privacy advocate.
The SPP extension has at last enabled us to compare what's in front of the curtain with what's behind it. Out front, we find a grand, feelgood gloss, extending around us a warm hug of protection. But behind the curtain, it's just another cybertech company pimping us out to the preds. You may say that terminology is strong, but the likes of 1PlusX, Criteo and Mather Analytics are weapons-grade predators - all of them blacklisted by uBlock Origin. Taking the trouble to auth them up for full access and cookie drops is about as close to pimping us out that a browser extension can get. A disgrace.
Far from protecting our privacy, Startpage Privacy Protection has gone out of its way to green-light known privacy threats. And why would the picture behind Startpage search's curtain look any different from the one behind SPP's?